How to build Caido passive workflows to scan all HTTP requests & responses…
In this tutorial, I will guide you through the steps to build your custom Caido Workflows, which can help you identify bugs based on your methodology…
You can scan for patterns like API keys or tokens, or take it to the next level by integrating it with “Match & Replace” rules to inject payloads and match for high-impact bugs, such as OS command injection.
Steps to create a new workflow
There are two types of Caido workflows:
Passive workflows will run on all requests that will pass through Caido.
Active workflows will wait until you choose a request and run that workflow manually on it.
In this tutorial, we will create a simple “passive workflow” that will scan for JWTs (JSON Web Tokens) in all responses. When it finds a token, it assigns the request a special color and creates a new finding.
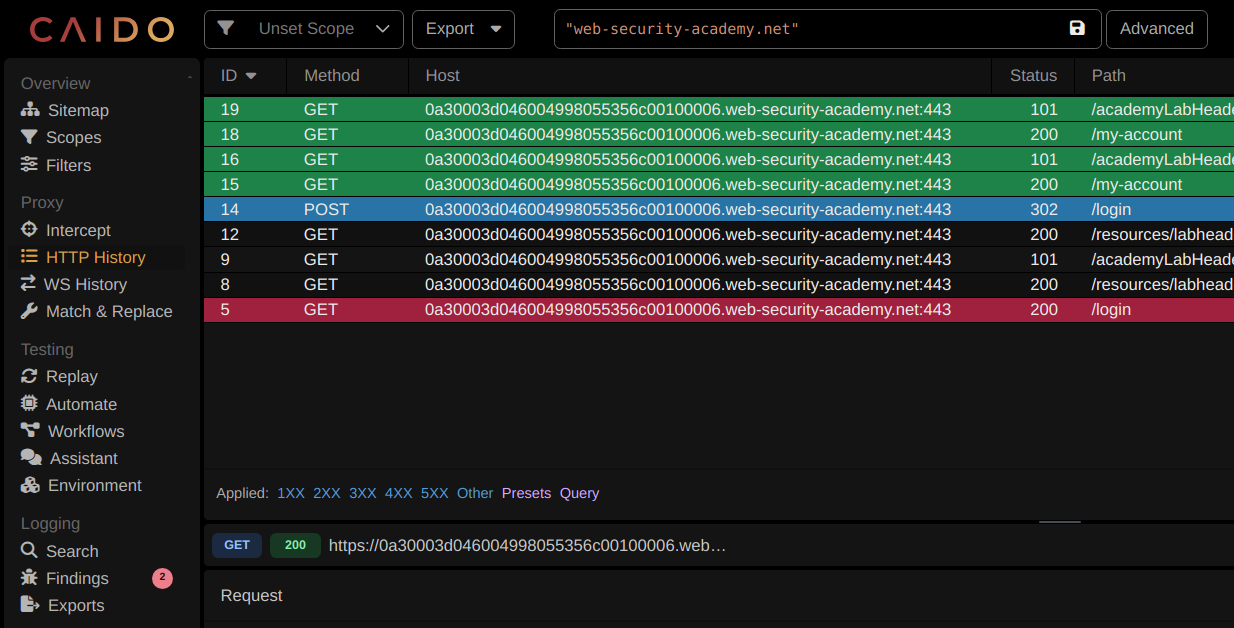
First, go to the “Workflows tab”, choose the passive tab, and click “New Workflow”
By default, you will find the first step in the workflow layers as “On intercept request”; in our case, we want to scan the responses, so we will replace this first step with “On Intercept Response”.
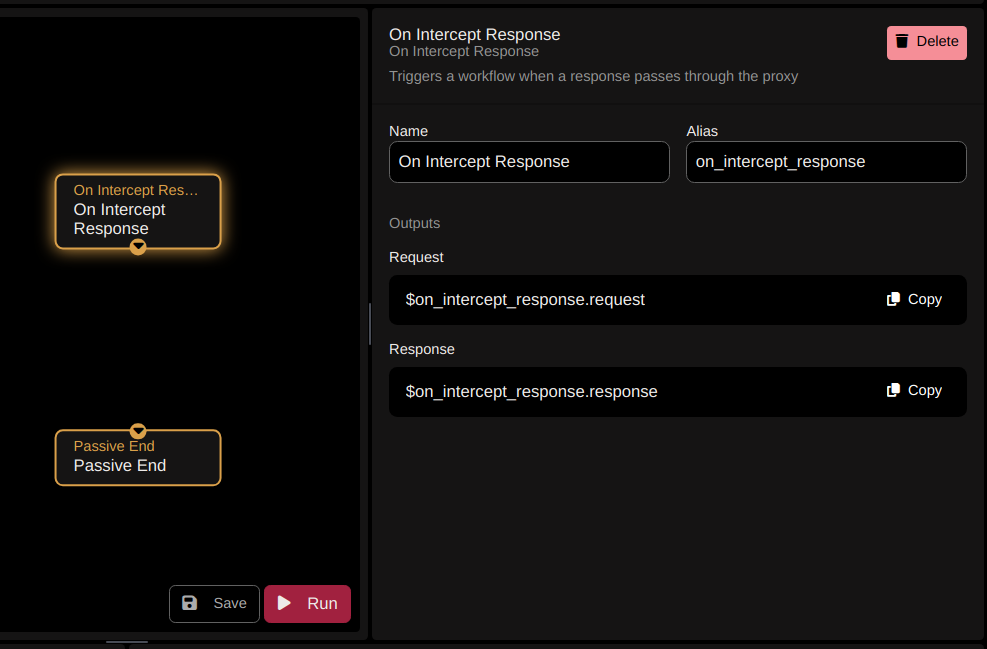
- The second step in the workflow is “Matches HTTPQL”. In the query (code), we will match for JWTs using the following regex query:
resp.raw.regex:/eyJ[a-zA-Z0-9]{10,}\.eyJ[a-zA-Z0-9]{10,}\.[a-zA-Z0-9_\-]{10,}/
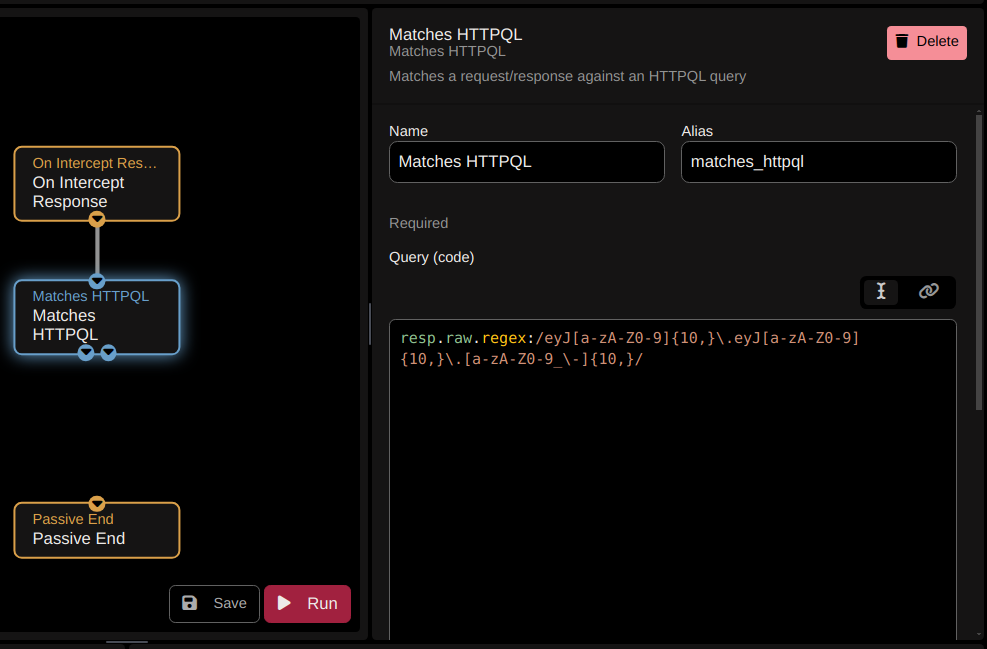
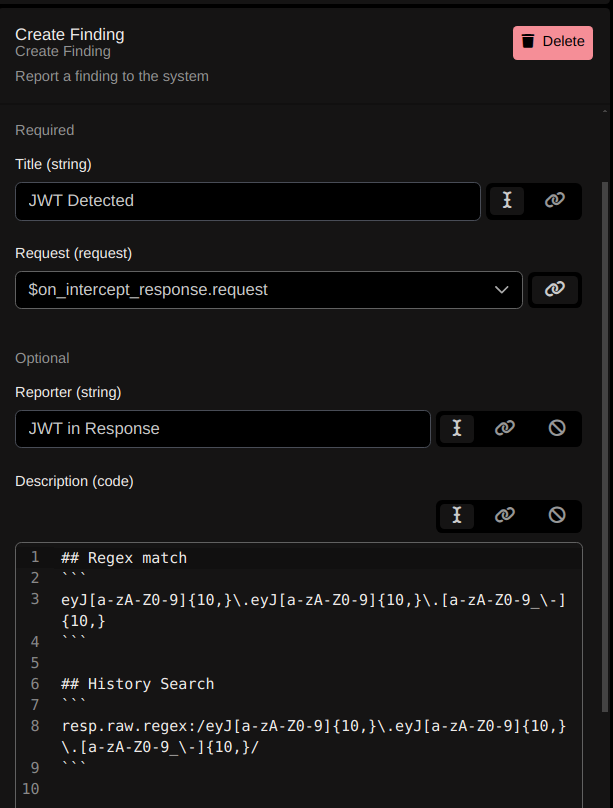
- After that, we will add the “Create Finding” and fill in the finding details like the following:
- The last step is the “Set Color” step, which will change the color of the request that matches the query in the HTTP history tab. Here we can use a website like https://htmlcolorcodes.com/ to choose our preferred colors. In this example, we can pick a blue color with code (#2874a6)
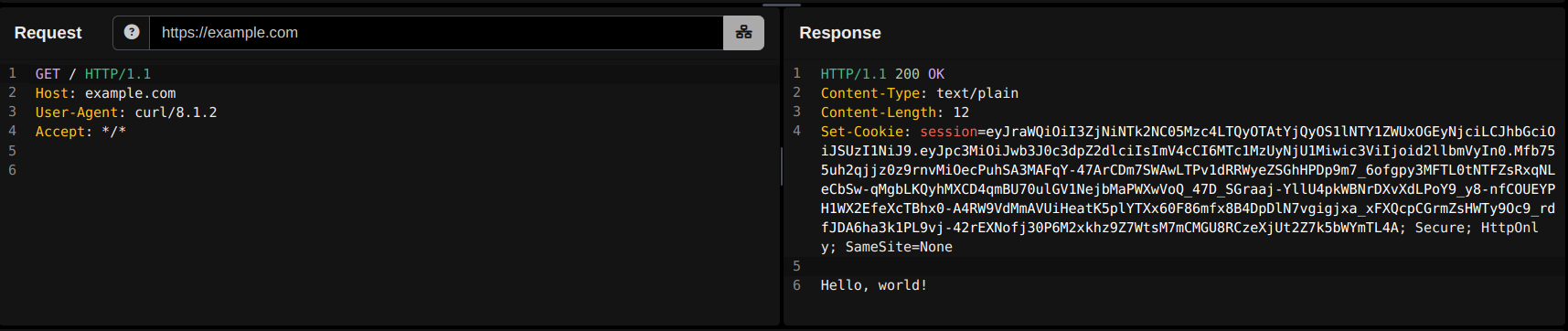
We can test the final setup with the new feature in Caido V0.50.0, or we can test it with the following JWT PortSwigger lab.
Finally, this is a very simple example to make it easy for you to set up your scans, which can be more advanced.
Additional Tip
If you want to test for bugs like IDOR (Insecure Direct Object Reference) or Web Cache Deception, you should test each endpoint that will respond with the user’s email address.
To easily filter these endpoints, you can create a new Caido passive workflow, but you will change the “Matches HTTPQL” to match the email that you used to create the account. Normally, if you are doing bug bounty, you will sign up with the platform’s hunting email, so I created the following HTTPQL regex query that will match for the hunting emails of HackerOne, Bugcrowd, and Intigriti.
resp.raw.regex:"([a-zA-Z1-9]{1,}[+]{0,1}[a-zA-Z1-9]{0,}@bugcrowdninja[.]com|[a-zA-Z1-9]{1,}[+]{0,1}[a-zA-Z1-9]{0,}@wearehackerone[.]com|[a-zA-Z1-9]{1,}[+]{0,1}[a-zA-Z1-9]{0,}@intigriti[.]me)"
If you don’t want to create a full Caido workflow, you can use this HTTPQL query in the Caido search tab to filter these endpoints quickly.
For more info on Caido workflows, you can take a look at the Caido docs.
If you want to follow for more -> https://x.com/__the7th